Trezor.io/Start – Your Ultimate Gateway to Crypto Security
Discover how Trezor.io/Start empowers you to protect, manage, and grow your crypto assets with complete security and independence.
🔐 What Is Trezor.io/Start?
Trezor.io/Start is the official onboarding platform for setting up your Trezor hardware wallet. It walks you through a secure setup process, ensuring your device, software, and firmware are authentic and uncompromised. This is the first step toward achieving true self-custody of your cryptocurrencies.
As a user, Trezor.io/Start is your digital safe zone — it guides you in protecting your recovery seed, installing Trezor Suite, and connecting your wallet to a clean, verified ecosystem.
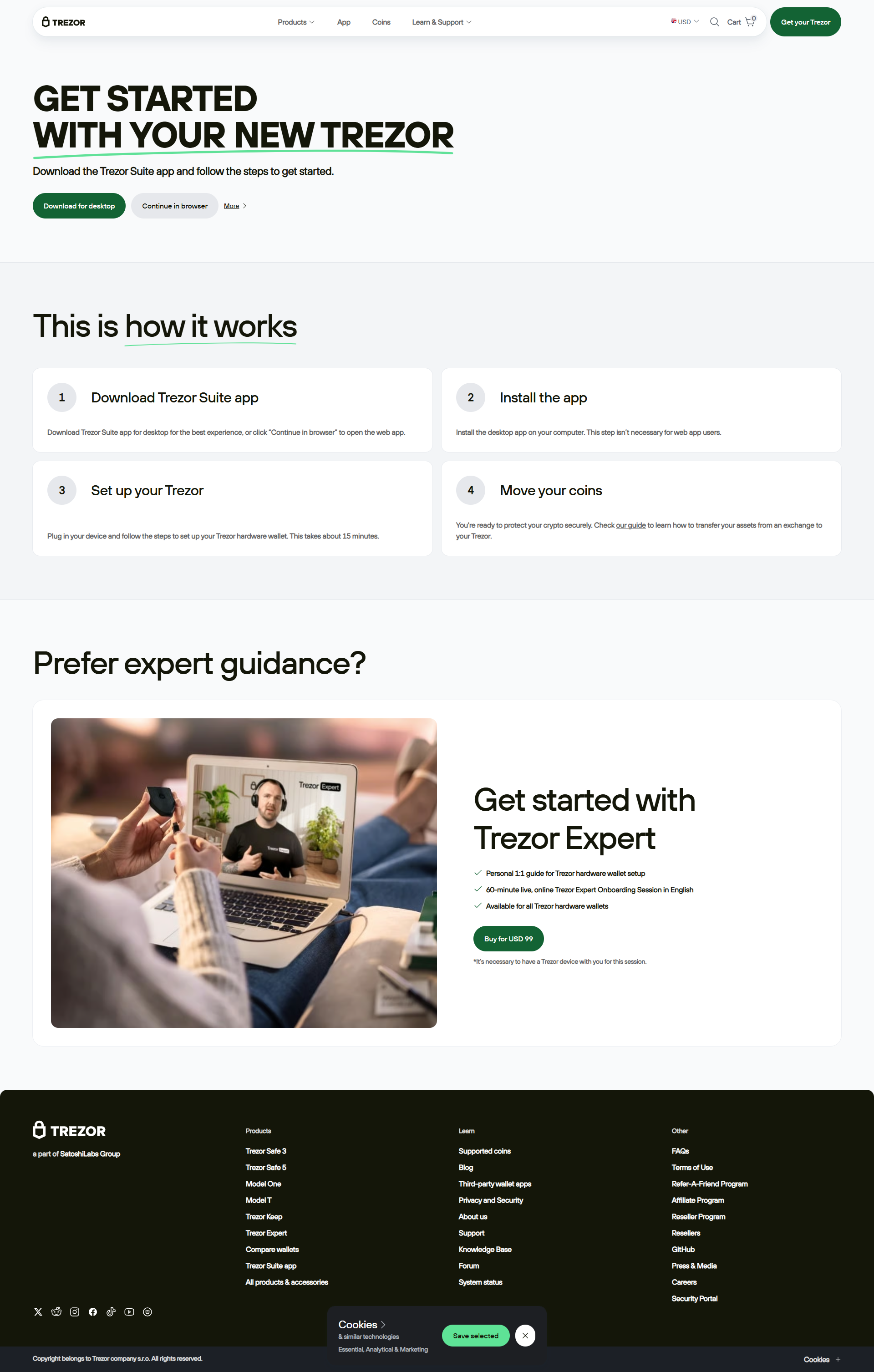
🧭 How to Use Trezor.io/Start (Step-by-Step)
- Visit Trezor.io/Start directly by typing it into your browser. Avoid search engines to prevent phishing attempts.
- Connect your Trezor device (Model T or One) using the official USB cable.
- Install Trezor Suite — your main dashboard for managing cryptocurrencies securely.
- Initialize your device and set up your PIN code. This ensures no one else can access your funds.
- Write down your recovery seed on paper (never digitally). Store it offline in a safe location.
- Explore Trezor Suite to send, receive, and manage multiple cryptocurrencies within a unified, secure interface.
🛡️ Self-Custody Simplified
At Trezor.io/Start, users take control of their digital wealth. Unlike exchange wallets, your private keys are stored offline — in your hands, not someone else’s servers.
This eliminates third-party risks, aligning perfectly with the core principle of crypto: “Be your own bank.”
⚙️ Complete Security Architecture
Trezor devices use open-source firmware, verified through the official Trezor.io/Start setup page. Each firmware update is signed, ensuring authenticity before installation.
Even if your computer is infected, your crypto remains safe — all signing happens within the hardware wallet itself.
💡 Why Trezor.io/Start Matters in 2025
With rising cyberattacks, fake wallet apps, and phishing scams, the importance of secure onboarding cannot be overstated. Trezor.io/Start acts as the official verification checkpoint between users and their devices.
It ensures that you’re not downloading malware, connecting to fake support sites, or installing rogue firmware. Everything happens within a trusted, encrypted environment.
📊 Trezor vs Software Wallets: A Quick Comparison
| Feature | Trezor Hardware Wallet | Software Wallet |
|---|---|---|
| Private Key Storage | Offline, Encrypted Chip | Online, Exposed to Threats |
| Firmware Verification | Through Trezor.io/Start | Not Always Possible |
| Security Level | Bank-Grade Protection | Vulnerable to Hacks |
| Ideal For | Long-Term Storage | Daily Transactions |
🧠 Security Best Practices for Trezor.io/Start Users
- Always verify the URL — https://trezor.io/start — before entering sensitive information.
- Use the official USB cable and avoid public computers.
- Keep your recovery seed offline and never share it with anyone.
- Enable the passphrase feature for extra protection.
- Regularly check for firmware updates through Trezor Suite.
These steps ensure your Trezor wallet remains uncompromised while maintaining complete control over your digital wealth.
💬 Expert Tip
“The real beauty of Trezor.io/Start lies in education. It’s not just about setting up a wallet — it’s about understanding what it means to truly own your crypto.”
— Blockchain Security Advisor, 2025
❓ Frequently Asked Questions (FAQs)
Do I need to connect to the internet to use Trezor.io/Start?
Yes, but only for accessing the official setup page. Your private keys and signing operations remain fully offline.
Can I use Trezor.io/Start with any computer?
Yes. It’s compatible with Windows, macOS, and Linux, provided you use updated browsers like Chrome or Firefox.
Is Trezor.io/Start secure from phishing?
Absolutely — as long as you type the official URL yourself and avoid fake lookalike websites.